Ipbx on Amazon EC2
From Taridium
| (8 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
[[File:ami-logo.png|right]] | [[File:ami-logo.png|right]] | ||
| + | |||
| + | These instructions will help you get started with ipbx v2 on Amazon's Elastic Compute Cloud. If everything goes well, you should be up and running with a fully featured VoIP PBX within a few minutes. | ||
| + | |||
| + | __TOC__ | ||
| + | |||
== Getting Started == | == Getting Started == | ||
| - | If you already know about Amazon Machine Instances, you can start ipbx on your account here: | + | If you already know about Amazon Machine Instances, you can start ipbx on your Amazon EC2 account here: |
[https://aws.amazon.com/amis/taridium-ipbx-free-5-user-edition Start your ipbx Amazon Machine Instance] | [https://aws.amazon.com/amis/taridium-ipbx-free-5-user-edition Start your ipbx Amazon Machine Instance] | ||
| + | |||
| + | Afterwards, skip to the [[#Security Group|Security Group]] section to review any security settings. | ||
=== What is Amazon EC2? === | === What is Amazon EC2? === | ||
| Line 23: | Line 30: | ||
====Launching the Instance==== | ====Launching the Instance==== | ||
| - | + | You can search for our instance image by entering the following ID: '''ami-4ea60427''' | |
| + | |||
| + | [[File:ami-select.png]] | ||
Click on '''Continue''' and select the appropriate settings for your environment (e.g. default settings). | Click on '''Continue''' and select the appropriate settings for your environment (e.g. default settings). | ||
| Line 54: | Line 63: | ||
[[File:warning.gif]]'''Caution''' | [[File:warning.gif]]'''Caution''' | ||
| - | The quicklaunch-x security group enables all IP addresses to access your instance over the specified ports (e.g., SSH for Linux/UNIX). This is acceptable for | + | The quicklaunch-x security group enables all IP addresses to access your instance over the specified ports (e.g., SSH for Linux/UNIX). This is acceptable for basic access, but might be unsafe for production environments. In production, you'll authorize only a specific IP address or range of addresses to access your instance. |
| + | |||
| + | [[File:ami-security.png]] | ||
Review your settings, and click Launch to launch the instance. | Review your settings, and click Launch to launch the instance. | ||
| Line 77: | Line 88: | ||
[admin@mymachine ~]# ssh -i mykey.pem root@ec2-XX-XX-XXX-XXX.compute-1.amazonaws.com | [admin@mymachine ~]# ssh -i mykey.pem root@ec2-XX-XX-XXX-XXX.compute-1.amazonaws.com | ||
| + | |||
| + | == Connecting SIP devices == | ||
| + | |||
| + | By default your EC2 instance will be configured with a private IP address. In order to successfully connect any SIP devices, make sure your '''externip''' parameter is set to the external IP address of your Amazon EC2 instance. You can also review the [[Network_Firewall_Configuration#SIP_Protocol|SIP Protocol Configuration]] page for further details on SIP NAT traversal configuration. | ||
== Next Steps == | == Next Steps == | ||
Continue [[Initial_Configuration|here]] to start with configuring your ipbx system. | Continue [[Initial_Configuration|here]] to start with configuring your ipbx system. | ||
Latest revision as of 15:24, 22 July 2014
These instructions will help you get started with ipbx v2 on Amazon's Elastic Compute Cloud. If everything goes well, you should be up and running with a fully featured VoIP PBX within a few minutes.
Contents |
Getting Started
If you already know about Amazon Machine Instances, you can start ipbx on your Amazon EC2 account here: Start your ipbx Amazon Machine Instance
Afterwards, skip to the Security Group section to review any security settings.
What is Amazon EC2?
Amazon Elastic Compute Cloud (Amazon EC2) is a web service that provides resizable compute capacity in the cloud. It is designed to make web-scale computing easier for developers. Read more about Amazon EC2 here.
Pre-Requisites
You will need an Amazon.com account and you need to sign up for EC2 services. Follow the instructions here if you haven't done so yet:
Getting Started with ipbx on EC2
Now that you're signed up for Amazon EC2, you're ready to launch an ipbx instance using the AWS Management Console.
Sign in to the AWS Management Console and open the Amazon EC2 console at https://console.aws.amazon.com/ec2/.
Use the email address and password you used when signing up for Amazon EC2.
Launching the Instance
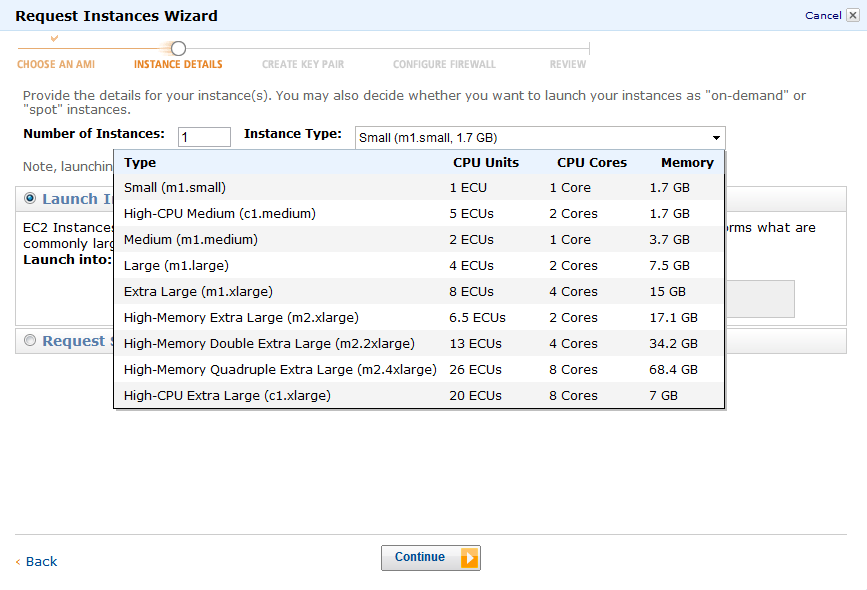
You can search for our instance image by entering the following ID: ami-4ea60427
Click on Continue and select the appropriate settings for your environment (e.g. default settings).
Create an SSH Key Pair
Under Choose a Key Pair, you can choose from any existing key pairs that you have created, or you can create a new one. For this example, we’ll create a key pair:
Do not select the None option. If you launch an instance without a key pair, you will not be able to connect to your instance. Click Create new Key Pair.
Type a name for your key pair and then click Download. You will need the contents of the private key to connect to your instance once it is launched. Amazon Web Services does not keep the private portion of key pairs.
Save the private key in a safe place on your system. Note the location because you'll need the key to connect to the instance.
Click Continue to view the settings that your instance will launch with.
Security Group
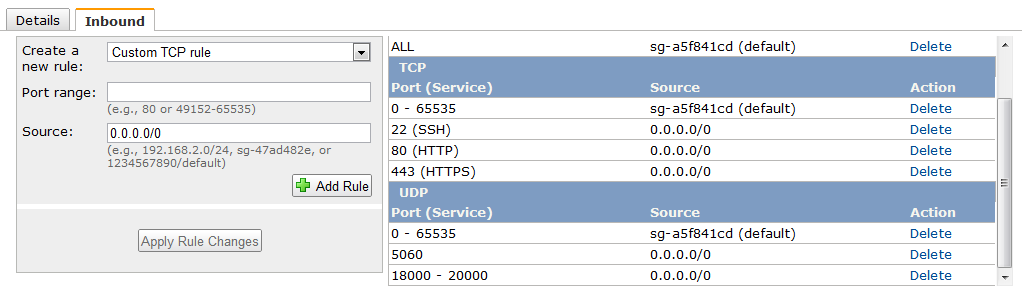
Under Security Details, in Security Group, the wizard automatically makes a security group selection for you, but you will need to add some additional ports to the default settings in order to have a fully working ipbx system.
A security group defines firewall rules for your instances. These rules specify which incoming network traffic will be delivered to your ipbx instance. All other traffic is ignored.
If you're new to Amazon EC2 and haven't set up any security groups yet, AWS defines a default security group for you. The name and description for the group is quicklaunch-x where x is a number associated with your quicklaunch group. The first security group you create using the Quick Launch Wizard is named quicklaunch-1. You can change the name and description using the Edit details button. For example, in this tutorial we changed the name to quicklaunch-0. The group already has basic firewall rules that enable you to connect to the type of instance you choose. For the ipbx instance, you connect through SSH on port TCP 22 and TCP 80 (WEB). The quicklaunch-x security group automatically allows SSH traffic on port 22. Add Port TCP 80 and ports UDP 5060-5070 (SIP), port UDP 4569 (IAX2) and ports UDP 18000-20000 (RTP) to your policy to enable VoIP traffic.
If you have used Amazon EC2 before, the wizard looks for an existing security group for the type of instance you’re creating.
The quicklaunch-x security group enables all IP addresses to access your instance over the specified ports (e.g., SSH for Linux/UNIX). This is acceptable for basic access, but might be unsafe for production environments. In production, you'll authorize only a specific IP address or range of addresses to access your instance.
Review your settings, and click Launch to launch the instance.
A confirmation page lets you know your instance is launching. Click Close to close the confirmation page.
In the Navigation pane, click Instances to view the status of your instance. It takes a short time for an instance to launch. The instance's status will be pending while it's launching.
After a short period, the status of your instance switches to running. You can click Refresh to refresh the display.
Record the Public DNS name for your instance because you'll need it for the next task. If you select the instance, its details (including the public DNS name) are displayed in the lower pane. You can also click Show/Hide in the top right corner of the page to select which columns to display.
(Optional) After your instance is launched, you can view the quicklaunch-x security group rule that was created.
On the Amazon EC2 console, under Network and Security, click Security Groups.
Click the quicklaunch-x security group and you can view the security rules created.
Connecting via SSH
Use your previously created or uploaded SSH private key to connect to your ipbx instance by specifying the key with the -i option and your instance DNS name:
[admin@mymachine ~]# ssh -i mykey.pem root@ec2-XX-XX-XXX-XXX.compute-1.amazonaws.com
Connecting SIP devices
By default your EC2 instance will be configured with a private IP address. In order to successfully connect any SIP devices, make sure your externip parameter is set to the external IP address of your Amazon EC2 instance. You can also review the SIP Protocol Configuration page for further details on SIP NAT traversal configuration.
Next Steps
Continue here to start with configuring your ipbx system.